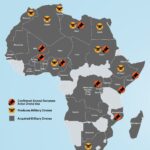
STATE VS. NON-STATE CYBER ACTORS IN AFRICA
In July 2023, Kenya’s eCitizen platform went dark bringing public services across the country to a grinding halt, it wasn’t just a temporary disruption, it was a wake-up call. A distributed denial-of-service (DDoS) attack, allegedly by pro-Russian hackers, had disabled access to everything from passport applications to business registrations. In a continent pushing fast toward digital government, the message was clear: Africa’s cyber vulnerabilities was exposed first-hand.
Driving this surge are a mix of factors: rapid internet adoption, weak digital infrastructure, and limited public awareness about online safety. These conditions have created fertile ground for both state-sponsored cyber actors and non-state criminal groups. While their motives differ geopolitical leverage versus financial gain their operations increasingly overlap, posing a complex and evolving threat landscape.
Related Article: THE EVOLVING CYBERSECURITY FRONTIER IN AFRICA
At the state level, cyber operations are becoming a preferred tool of influence and espionage. Governments or their proxies are targeting strategic sectors such as energy, telecommunications, and public institutions to collect intelligence, disrupt rivals, or gain diplomatic leverage. These attacks are often carried out by well-funded, technically advanced groups known as Advanced Persistent Threats (APTs), which use stealthy techniques like modular malware and spear-phishing to maintain long-term access.
For example, in May 2023, Chinese-linked hackers reportedly infiltrated several key ministries within Kenya’s government including the president’s office to gather sensitive data related to the country’s debt obligations to Beijing. Less than two years later, in April 2025, hackers associated with Algeria breached Morocco’s National Social Security Fund and leaked critical data in what analysts believe was a geopolitically motivated attack.
These state-sponsored attacks are not isolated cases. They reflect a larger pattern of cyber power projection across the continent, where foreign interests increasingly intersect with Africa’s growing digital and geopolitical importance.
On the other hand, non-state actors dominate the cybercrime landscape with financially driven attacks. These range from phishing scams and ransomware to business email compromise (BEC) schemes and social engineering. Unlike state actors who plan long-term campaigns, these criminals move quickly, exploiting everyday weaknesses in security systems, often using tools that require minimal technical skill.
Groups like Nigeria’s Black Axe have orchestrated widespread scams that extend well beyond African borders, while the rise of ransomware-as-a-service has lowered the bar for launching devastating attacks. In February 2024, South Africa’s Government Employees Pension Fund was targeted by the notorious Lock Bit group, compromising personal and financial data for millions.
Even public infrastructure isn’t safe. In July 2023, a pro-Russian group carried out a distributed denial-of-service (DDoS) attack against Kenya’s eCitizen platform, effectively halting government services for days. Meanwhile, online scams from romance frauds to digital sextortion continue to siphon millions of dollars and wreak personal havoc, especially among vulnerable users.
When comparing state and non-state actors, the differences are clear but narrowing. State-backed groups enjoy superior technical capabilities and long-term strategies, but increasingly, some cybercriminals are adopting similar methods, using artificial intelligence to scale phishing campaigns or mimicking state tactics to prolong access. Meanwhile, some states may be outsourcing operations to criminal groups to maintain plausible deniability.
Recent trends highlight the urgency: between 2024 and 2025, there was a 21% increase in business-targeted cyber threats across Africa, while spyware detections more than doubled. The proliferation of AI tools, unpatched systems, and widespread cloud adoption have only magnified the risks.
The impact of these threats is far-reaching. Economically, Africa ranks among the top three most affected regions globally by ransomware, with essential services in health and telecommunications frequently targeted. Politically, cyber-espionage has the potential to erode national sovereignty and influence diplomatic relations, especially in debt negotiations or during elections.
Yet attribution remains one of the biggest challenges. Cyberattacks are often conducted anonymously, leaving few forensic breadcrumbs. Limited technical capabilities within local law enforcement make it difficult to respond effectively, and in many cases, victims remain silent either out of embarrassment or fear of reputational damage.
These vulnerabilities are exacerbated by global and regional power dynamics. The 2018 breach of the African Union headquarters allegedly carried out by Chinese operatives remains a powerful reminder of how digital insecurity can intersect with political dependency and surveillance.
In response, African nations are beginning to strengthen their defences. Some are forming regional alliances, signing international agreements, and improving cybercrime legislation. However, much more is needed. Policymakers must invest in national incident response teams, diversify technology suppliers to reduce overdependence, and ratify frameworks like the Malabo Convention to create unified continental standards.
Public-private partnerships will also play a crucial role. Tech companies, telecom providers, and civil society groups must work alongside governments to boost public awareness, share threat intelligence, and develop localized solutions. Investing in cybersecurity education and training is equally vital to build a skilled workforce capable of defending the continent’s digital future.
King Richard Igimoh, Group Editor ALO
King Richard Igimoh, Group Editor African Leadership Organisation is an award-winning journalist, editor, and publisher with over two decades of expertise in political, defence, and international affairs reporting. As Group Editor of the African Leadership Organisation—publishers of African Leadership Magazine, African Defence & Security Magazine, and Africa Projects Magazine—he delivers incisive coverage that amplifies Africa’s voice in global security, policy, and leadership discourse. He provides frontline editorial coverage of high-profile international events, including the ALM Persons of the Year, the African Summit, and the African Business and Leadership Awards (ABLA) in London, as well as the International Forum for African and Caribbean Leadership (IFAL) in New York City during the United Nations General Assembly.
Recent Posts
Categories
- Air & Aerospace17
- Border Security15
- Civil Security6
- Civil Wars4
- Crisis5
- Cyber Security8
- Defense24
- Diplomacy19
- Entrepreneurship1
- Events5
- Global Security Watch6
- Industry8
- Land & Army9
- Leadership & Training5
- Military Aviation7
- Military History27
- Military Speeches1
- More1
- Naval & Maritime9
- Policies1
- Resources2
- Security12
- Special Forces2
- Systems And Technology9
- Tech6
- Uncategorized6
- UNSC1
- Veterans7
- Women in Defence9
Related Articles
RETHINKING HUMAN SECURITY IN AFRICA’S CHANGING DIPLOMATIC LANDSCAPE
Africa’s diplomatic and security thinking is undergoing a quiet but significant shift....
ByKing Richard Igimoh, Group Editor ALODecember 30, 2025AFRICA’S CYBERSECURITY STANDING IN A HIGH-RISK DIGITAL AGE
Africa’s rapid digital expansion has brought economic opportunity, but it has also...
ByKing Richard Igimoh, Group Editor ALODecember 29, 2025SKIES OF ALLIANCE: HOW JOINT AIR EXERCISES RESHAPED GLOBAL AEROSPACE SECURITY IN 2025
From July 10 to August 8, 2025, the U.S. Pacific Air Forces...
ByKing Richard Igimoh, Group Editor ALODecember 16, 2025AFRICA’S DIGITAL FORTRESS: HOW THE CONTINENT IS BUILDING CYBERSECURITY LAWS IN AN AGE OF RANSOM AND ESPIONAGE
From Cape Town to Cairo, African governments are racing to enact cybersecurity...
ByKing Richard Igimoh, Group Editor ALONovember 24, 2025